Understanding Cybersecurity Compliance: Safeguarding Your Business Against Digital Threats
While the term “cybersecurity compliance” may conjure images of complex regulations and intricate technical requirements, it’s crucial to recognize that compliance standards are crafted with a purpose – to guard your business against an ever-changing landscape of digital threats.
Rather than being a daunting endeavor, compliance serves as a proactive approach to mitigate risks and protect sensitive data. By unraveling the idea of cybersecurity compliance, businesses can gain a comprehensive understanding of the measures required to establish a resilient security posture.
The reality is that embracing any technology will bring inevitable exposure to a constantly shifting landscape of cyber threats and vulnerabilities, which demands a proactive stance and vigilant attention. This is where the significance of cybersecurity compliance comes into play: it provides a framework carefully designed within regulatory bounds to strengthen the security of your organization’s most invaluable assets – its data.
The Significance of Cybersecurity Compliance
Safeguarding Business Integrity: Cybersecurity compliance is not merely a regulatory formality; it’s a fundamental commitment to the integrity of your business operations. By adhering to established frameworks, organizations signal their dedication to safeguarding the trust of customers, partners, and stakeholders alike.
Mitigating Financial Losses: The consequences of non-compliance with cybersecurity standards can be financially devastating. In the event of a breach, the costs associated with remediation, legal proceedings, and potential fines can cripple even the most robust enterprises. Moreover, the loss of revenue due to downtime and diminished customer confidence can have far-reaching implications.
Legal Ramifications: Non-compliance with cybersecurity regulations exposes businesses to a host of legal penalties. Regulatory bodies worldwide are enacting stricter measures to hold organizations accountable for lapses in data protection. From hefty fines to potential legal action, the legal ramifications of non-compliance can be severe and long-lasting.
Preserving Reputation: Reputation takes years to build but can be lost in an instant. A cybersecurity breach not only jeopardizes sensitive data but also undermines the trust that customers and partners place in your organization. The resulting reputational damage can have lasting effects on customer loyalty and brand perception.
Fostering a Culture of Security: Cybersecurity compliance is more than just a checkbox exercise. It promotes a security culture within the organization, encouraging employees to be vigilant and proactive in safeguarding sensitive information. This heightened awareness serves as a formidable defense against potential threats.
Gaining a Competitive Edge: Demonstrating robust cybersecurity measures can be a differentiator in an increasingly security-conscious marketplace. Customers and partners are more likely to engage with organizations prioritizing data protection, viewing them as reliable defenders of sensitive information.
Understanding Specific Regulations
NIST Framework: A Risk-Based Approach to Cybersecurity
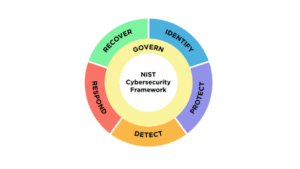
The National Institute of Standards and Technology (NIST) Framework is a comprehensive guide for organizations to manage and reduce cybersecurity risk. One of the standout features of this framework is its advocacy for a risk-based approach. Instead of employing a one-size-fits-all strategy, organizations are encouraged to assess their unique threats and vulnerabilities. This empowers them to allocate resources where they are most needed, ensuring that cybersecurity efforts are focused on the areas with the highest potential impact.
The Five Core Functions
Central to the NIST Framework are its five core functions, each representing a crucial aspect of cybersecurity strategy:
- Identify: This initial phase involves cataloging assets, identifying vulnerabilities, and comprehending the potential consequences of cybersecurity risks. By gaining a deep understanding of their environment, organizations lay the groundwork for effective risk management.
- Protect: Once vulnerabilities are identified, the next step is to implement protective measures. This encompasses everything from access controls and data encryption to secure architecture and continuous monitoring. The goal is to establish robust defenses that safeguard against both internal and external threats.
- Detect: Real-time monitoring and detection capabilities are vital in any effective cybersecurity strategy. This function focuses on swiftly identifying any breaches or anomalies within the network. Early detection enables organizations to respond promptly, mitigating potential damage.
- Respond: In the event of a cybersecurity incident, a rapid and coordinated response is paramount. The Respond function outlines the steps to take when an incident occurs, including containing the breach, eradicating the threat, and restoring normal operations.
- Recover: After an incident, the focus shifts towards recovery and restoration. This involves restoring systems and data to their previous state, learning from the incident to bolster future defenses, and ensuring that operations resume smoothly.
By meticulously following this structured approach, organizations enhance their cybersecurity resilience. They not only establish robust defensive measures but also develop the capacity to adapt and evolve in the face of emerging threats. This adaptability is crucial in an ever-changing cybersecurity landscape where new risks constantly emerge.
GDPR: Protecting Data Privacy and Individual Rights
The General Data Protection Regulation (GDPR) represents a landmark in data protection and privacy regulations. Enforced by the European Union, it places a profound emphasis on the rights of individuals regarding their personal data.
GDPR mandates that organizations handle data transparently, ensuring explicit consent is obtained for data processing. Additionally, individuals have the right to access, rectify, and erase their personal information. Failure to comply with GDPR can result in substantial fines, reinforcing its significance in global data protection efforts.
HIPAA: Safeguarding Healthcare Data and Patient Privacy
The Health Insurance Portability and Accountability Act (HIPAA) is paramount in the healthcare industry. It addresses the security and privacy of patients’ medical information. HIPAA mandates strict controls on handling Protected Health Information (PHI). Covered entities, such as healthcare providers and insurers, must implement robust security measures to safeguard patient data. Non-compliance with HIPAA can lead to severe penalties, making adherence crucial for healthcare organizations.

PCI DSS: Ensuring Secure Handling of Payment Card Data
The Payment Card Industry Data Security Standard (PCI DSS) is essential for businesses that handle payment card information. Developed by major credit card companies, PCI DSS outlines comprehensive requirements to secure cardholder data during processing, transmission, and storage. Compliance is divided into various levels, depending on the transaction volume. Non-compliance may result in fines, reputation loss, and even card processing privileges revocation.
ISO 27001: Internationally Recognized Information Security Standard
The ISO 27001 standard is globally acknowledged as the gold standard for Information Security Management Systems (ISMS). It provides a systematic approach to managing and protecting sensitive information. ISO 27001 mandates a risk-based approach, requiring organizations to identify and assess potential security risks. By implementing controls and continuously monitoring them, organizations enhance their ability to safeguard information assets and demonstrate their commitment to information security.
CMMC: Elevating Cybersecurity Maturity
The Cybersecurity Maturity Model Certification (CMMC) is a comprehensive framework developed by the U.S. Department of Defense (DoD) to enhance cybersecurity measures across the defense industrial base (DIB). It represents a significant evolution in cybersecurity requirements for contractors and subcontractors who work with the DoD. Unlike its predecessor, the Defense Federal Acquisition Regulation Supplement (DFARS) framework, which focused primarily on self-assessments, CMMC introduces a tiered approach based on five levels of maturity, each building on the requirements of the previous level.
CMMC represents a paradigm shift in how cybersecurity compliance is approached within the defense industrial base. By moving from self-assessments to third-party assessments conducted by certified assessors, CMMC ensures a higher level of rigor and accountability. This transition not only raises the bar for cybersecurity practices but also establishes a standardized and objective measure of an organization’s cybersecurity maturity.
Furthermore, CMMC has a ripple effect across the entire supply chain. As prime contractors require their subcontractors to meet specific CMMC levels, it creates a cascading effect, driving improvements in cybersecurity practices throughout the defense contracting ecosystem. This collaborative approach strengthens the overall cybersecurity posture of the defense industrial base, better protecting the nation’s critical information and technology assets.
These regulatory frameworks collectively form the backbone of modern cybersecurity compliance efforts. Understanding and adhering to these standards ensures legal and regulatory compliance and reinforces an organization’s commitment to data protection, privacy, and overall cybersecurity resilience.
How to Achieve Cybersecurity Compliance
Achieving and maintaining compliance is not merely a checkbox exercise; it’s an ongoing commitment to strengthen your organization against evolving threats. Here are key steps and best practices to guide you on this crucial journey:
Conduct Risk Assessments
One of the foundational steps in achieving cybersecurity compliance is conducting comprehensive risk assessments. This process involves identifying, evaluating, and prioritizing potential risks and vulnerabilities within your organization’s infrastructure. Understanding the specific threats that could impact your operations allows you to customize your compliance efforts to target the most critical areas. Regularly revisiting and updating risk assessments ensures compliance measures remain in sync with the ever-changing threat landscape.
Relying on the expertise of cybersecurity professionals can significantly enhance your risk assessment process and give you peace of mind. Cybersecurity experts employ advanced techniques and tools to conduct thorough evaluations, providing valuable insights into potential vulnerabilities and areas of improvement. Their specialized knowledge and experience are crucial in ensuring the effectiveness and accuracy of your risk assessments.
Implement Security Controls and Policies
Once risks have been identified, the next step is to implement robust security controls and policies. These measures act as the safeguards that protect your organization’s digital assets. Security controls may encompass a range of strategies, from access controls and encryption protocols to network segmentation and intrusion detection systems. Policies, on the other hand, provide the guidelines and procedures that govern how these controls are applied and maintained.

Developing Incident Response Plans
No matter how robust your preventive measures are, it’s essential to be prepared for the possibility of a security incident. Developing a comprehensive incident response plan is crucial. This plan outlines the steps to be taken in the event of a security breach, including identification, containment, eradication, recovery, and lessons learned. Regular testing and simulation exercises help ensure your team is well-prepared to respond to real-world incidents.
If you need a hand with your incident response plan, download our free template here to get started.
Regular Security Audits and Assessments
Achieving and maintaining compliance is an ongoing effort requiring vigilant monitoring and evaluation. Regular security audits and assessments are crucial for the effectiveness of your compliance measures. These evaluations go beyond surface-level checks, delving into the intricacies of your systems and policies. They uncover potential vulnerabilities and areas for improvement, ensuring that your defenses remain robust.
Cybersecurity experts can conduct various assessments tailored to your organization’s needs. For instance, vulnerability assessments pinpoint specific weaknesses in your network or applications, providing a detailed roadmap for remediation. Penetration testing, on the other hand, involves simulated cyberattacks to evaluate the resilience of your defenses. When executed by professionals, these assessments produce actionable insights that strengthen your security posture.
Engaging with reputable cybersecurity firms or certified professionals can significantly enhance the effectiveness of your security audits and assessments. (We know someone who does a great job at this). Their expertise and knowledge of evolving threats equip them to conduct thorough evaluations, identifying glaring weaknesses and subtle vulnerabilities. This collaborative effort ensures that your compliance measures remain dynamic and responsive to emerging risks.
Employee Training and Awareness Programs
The human element plays a pivotal role in cybersecurity. Establishing robust employee training and awareness programs is paramount. These programs educate staff members on best practices, security protocols, and how to recognize and respond to potential threats. An informed and vigilant workforce is a critical line of defense against cyberattacks.
By diligently following these steps and best practices, organizations can achieve and sustain a strong cybersecurity compliance posture. Remember, compliance is not a one-time achievement but an ongoing commitment to the security and integrity of your digital assets.

Make Cybersecurity Compliance a Priority
By adhering to established frameworks like NIST, GDPR, HIPAA, PCI DSS, or ISO 27001, organizations meet legal obligations and foster trust among stakeholders, positioning themselves as responsible custodians of data. This trust, earned through demonstrable adherence to compliance standards, becomes a valuable asset in a world increasingly conscious of data security.
The benefits of investing in cybersecurity compliance extend beyond regulatory adherence. It encompasses enhanced data protection, improved customer trust, reduced cybersecurity risks, and a competitive edge in the market. These advantages collectively contribute to a resilient security posture crucial in today’s landscape, where cyber threats are ever-present and constantly evolving.
Remember, cybersecurity compliance is not just a checkbox to tick; it’s a commitment to your organization’s integrity, trust, and reputation. By embracing compliance as a strategic initiative, businesses strengthen their defenses and set the stage for sustained success in an increasingly digital-driven world. It’s a journey that organizations of all sizes and sectors must embark on to ensure their place in a secure and thriving digital future. If you’re looking for a cybersecurity expert to help you with compliance, contact Edge Networks today.

