Building a Secure Digital Environment with Cybersecurity Assessments
Imagine finding a piece of furniture that fits your home perfectly, but there’s a catch – you have to build it yourself. Sometimes we can get ahead of ourselves and dive into the assembly without even glancing at the instruction manual, resulting in an unstable, unreliable, and virtually unusable piece of furniture. It’s a familiar scenario for many, and the resulting frustration is all too real.
Cybersecurity often mirrors this furniture-building scenario. Just as assembling furniture requires careful planning, guidance, and understanding, so does fortifying your business against ever-evolving cyber threats. An organization that neglects to conduct proper cybersecurity assessments may find its information at risk, vulnerable to cyber threats, and potentially unstable.
What is a Cybersecurity Assessment?
Cybersecurity assessments serve as your company’s guardians, diligently protecting its most valuable assets. But what exactly are these assessments, and why are they essential? Cybersecurity assessments evaluate your organization’s digital infrastructure, policies, and practices.
These evaluations identify vulnerabilities, weaknesses, and potential risks that might expose your company to cyber threats. These assessments aim to fortify your defences, ensuring your sensitive data remains safe and secure from malicious actors.
Think of cybersecurity assessments as thorough health check-ups for your digital ecosystem. Just as you’d want to detect any hidden health issues early on to address them effectively, cybersecurity assessments allow you to uncover vulnerabilities and mitigate risks before they become major security breaches.
Why are Cyber Assessments Important?
Cybercriminals are constantly on the prowl, seeking loopholes to exploit and vulnerabilities to breach. Without proper assessment and guidance, your company’s security might resemble that unreliable furniture riddled with gaps and uncertainties.
By conducting cybersecurity assessments, you create a comprehensive safety net—a systematic approach to identify gaps, update outdated processes, and fortify your defences. These assessments protect sensitive information and serve as a shared foundation of understanding for everyone within your company, irrespective of their position.
One of the most significant advantages of conducting cybersecurity assessments is the potential to leverage them for acquiring cyber insurance or partnering with other organizations. Demonstrating a robust cybersecurity program mitigates risks and opens doors to new opportunities, fostering trust among potential partners and clients.
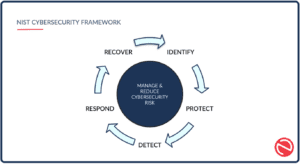
Overview of the NIST Cybersecurity Framework (NIST CSF):
Just like the frustration of attempting to build furniture without the guidance of an instruction manual, navigating the world of cybersecurity assessments can leave us feeling frustrated and exposed to potential risks. Thankfully, we have a trusted resource that serves as the ultimate instruction manual in the realm of cybersecurity – the National Institute of Standards and Technology (NIST). NIST plays a crucial role in providing guidance and frameworks to help organizations improve their cybersecurity posture.
One of its most notable contributions is the NIST Cybersecurity Framework (NIST CSF), a comprehensive set of guidelines, best practices, and risk management recommendations for organizations to better manage and reduce cybersecurity risks. NIST CSF was developed by cybersecurity experts and is a reliable and comprehensive reference when conducting a cybersecurity assessment.
The framework is like a well-structured blueprint that guides you through strengthening your company’s security defenses. It allows you to assess your current cybersecurity practices, identify areas for improvement, and develop a robust and effective security strategy.
What makes the NIST CSF a trusted standard in the cybersecurity world is its credibility. It’s the result of rigorous research, collaboration, and experience, making it a reliable and credible source for organizations seeking to enhance their cybersecurity measures.
The framework also offers flexibility, allowing organizations to tailor their security approach to their unique needs and challenges. Its adaptability makes it ideal for organizations of all sizes and industries.
The Five Functions of NIST CSF: Building A Strong Fortress
Within the NIST CSF, five core functions form the backbone of a successful cybersecurity program and work together to create a comprehensive cybersecurity strategy.
Identify
The first step in any cybersecurity assessment is the “Identify” phase, which helps lay the foundation of a strong fortress. During this critical stage, your cybersecurity team comprehensively reviews all organization assets, policies, and systems. Think of it as taking inventory of everything within your digital landscape—knowing what you have is the key to building an effective protection plan.
By identifying your company’s assets, potential risks, and vulnerabilities, your cybersecurity team gains invaluable insights into the areas that require heightened protection. It’s like understanding the weak points in your fortress walls and adding extra defenses.
Protect
With a clear understanding of your digital assets and risks, your cybersecurity team moves on to the “Protect” phase. Here, they determine the security measures to safeguard your company’s sensitive data and infrastructure from potential threats.
This phase is similar to installing layers of protective walls, gates, and moats around your fortress. It includes building an incident response plan and implementing awareness training for all employees, emphasizing the importance of cybersecurity best practices. Data security measures, such as encryption and secure data storage, fortify your company’s defenses against unauthorized access.
Another crucial protection aspect is access control, ensuring only authorized team members access critical data and systems. Just like assigning guards to protect the most sensitive areas of a fortress, access control limits entry to those who truly need it.
Detect
An impenetrable fortress must have vigilant guards, constantly monitoring for any signs of intrusion or danger. The “Detect” phase in the NIST CSF is comparable to setting up a network of vigilant monitoring systems.
Implementing advanced tools like anti-malware and intrusion detection systems serves as your digital watchdogs. They keep an eye on your network, alerting your cybersecurity team to any suspicious activities or potential threats. Prompt detection is crucial in mitigating damage and minimizing the impact of cyber incidents, much like catching an enemy at the gates before they can breach the walls.
Respond
Despite the best defenses, there’s always a possibility that an intruder might breach the fortress walls. This is where the “Respond” phase of the NIST CSF comes into play—your company’s crisis management plan in action.
Having a well-defined plan in place to handle security incidents is crucial. Your cybersecurity team ensures your company is prepared to respond promptly and efficiently. It includes technical responses and public relations strategies. Data breaches can have severe cost implications, damaging both finances and reputation, so a swift and effective response is essential.
Recover
Even with a strong defense and quick response, some damage might still occur. This is where the “Recover” phase is vital—post-incident actions to restore your company’s image and data security.
Recovering from a cybersecurity event involves assessing the impact of the incident, learning from it, and adapting your defenses accordingly. It’s about ensuring your company’s resilience and restoring normalcy. Just as a fortress rebuilds its walls after a siege, your company bounces back, stronger and more prepared than ever.
These five functions of the NIST CSF—Identify, Protect, Detect, Respond, and Recover—work together to form a comprehensive cybersecurity strategy. By taking inventory, building protective layers, monitoring for threats, responding swiftly, and recovering effectively, your company can stand firm against the ever-evolving landscape of cyber threats.

Investing in Cybersecurity
While NIST CSF provides an invaluable framework for conducting cybersecurity assessments, the process can be complex and dynamic. For this reason, partnering with a professional cybersecurity team is vital. A competent cybersecurity team can guide you through the entire process, ensuring no stone is left unturned in safeguarding your company’s digital assets.
These experts possess the knowledge, experience, and up-to-date insights needed to help you navigate the intricacies of cybersecurity assessments. They can also assist in interpreting assessment results and creating a tailored action plan to address any vulnerabilities discovered.
Ongoing Cybersecurity Assessments Keep You One Step Ahead
Cybersecurity assessments should not be a one-time exercise but an ongoing process that helps you regularly identify vulnerabilities, strengthen defenses, and protect your most valuable assets through comprehensive evaluations. Regular assessments allow you to stay one step ahead of cyber threats.
Your peace of mind and your company’s future are worth every effort. Contact us today if you’re searching for a holistic approach that ensures your cybersecurity strategy aligns with your organization’s unique needs and challenges.

