Endpoint Security: The Cutting Edge of Protection
Over the last few decades, we’ve seen technology evolve in leaps and bounds. We rely on it more and more for everyday purposes. However, this advancement has also brought risks. There are more dangers related to technology than ever before. As such, technological security has also been updating. Security software is an absolute must for your connected device. If you’re looking to be on the cutting edge of protection, you must know what you’re looking for. Keep reading to learn more about the benefits of endpoint security compared to traditional antivirus software.
What is Endpoint Security?
As the name implies, endpoint security focuses on securing endpoints or entry points of end-user devices. End-user devices are any connected devices you may own. This includes desktop computers, laptop computers, tablets, and even smartphones. These devices can be protected from malicious actors and campaigns using endpoint security.
This form of security protects devices on a network or in the cloud. It protects these devices from cybersecurity threats, including malware. Endpoint security is more sophisticated than traditional antivirus software. It needs to be, as it protects your information from being corrupted or stolen for malicious reasons.
Built for Organizations of All Sizes
Endpoint security is often seen as the frontline of cybersecurity efforts. When it comes to enterprise networks, it’s often the first place they look to secure. It helps protect organizations and individuals from the threat of security breaches from:
- Nation-states
- Hacktivists
- Organized crime
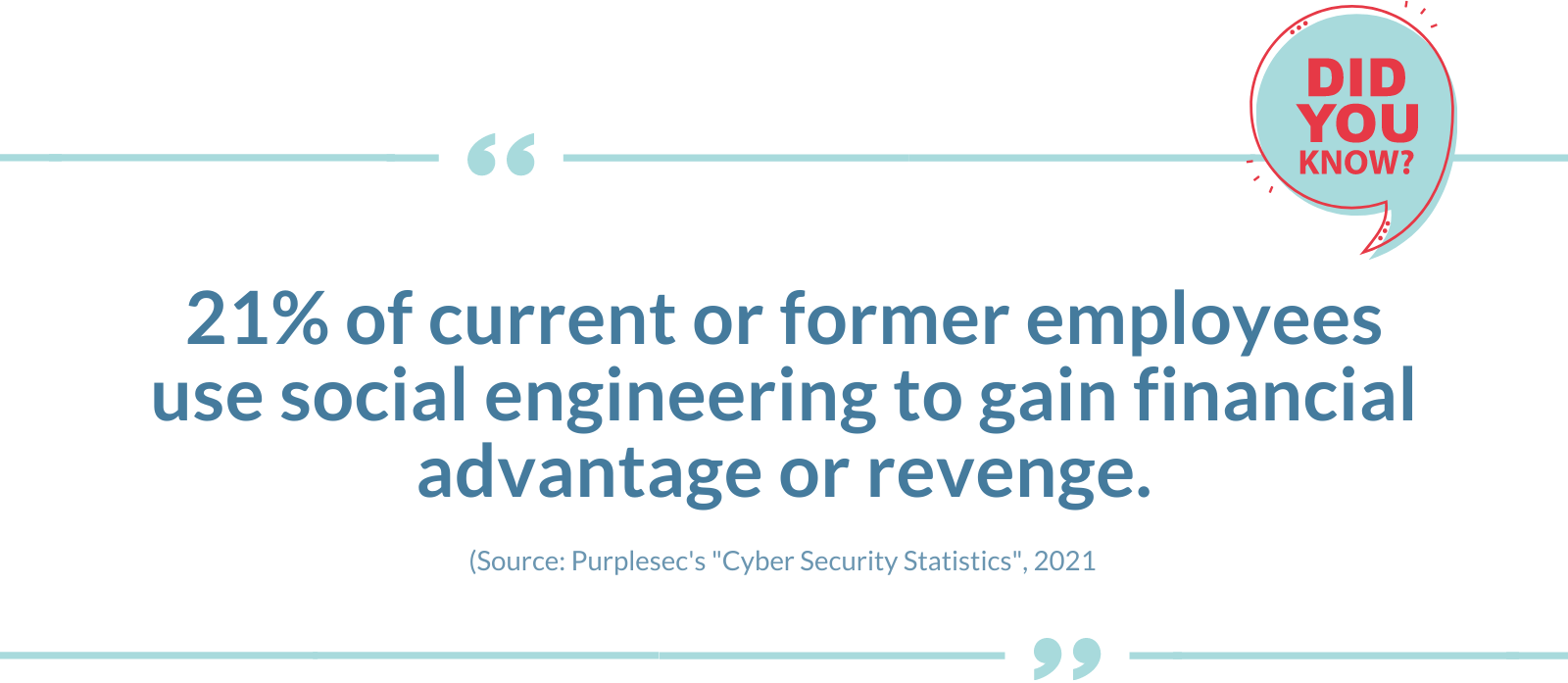
- Insider threats (both malicious and accidental)
Most endpoint security solutions are highly advanced. They quickly detect, analyze, block, and contain threats in progress. These software options collaborate with other technological systems and administrators to move things quickly and effectively.
Why is Endpoint Security Necessary?
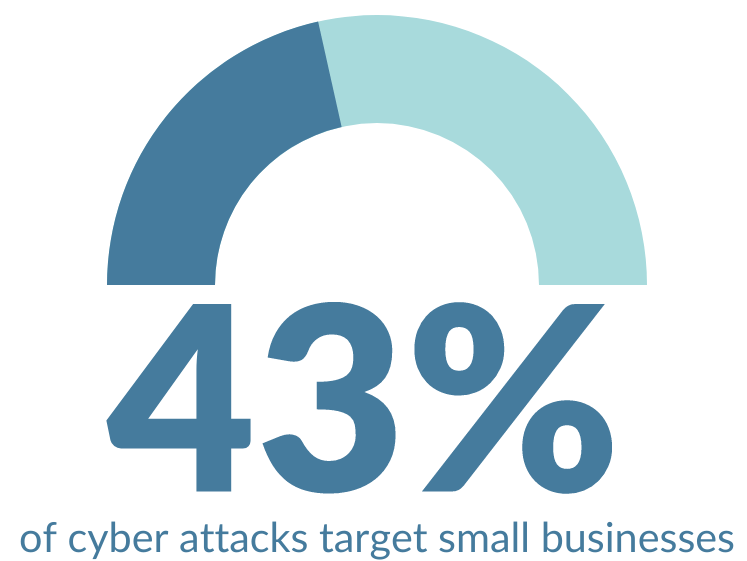
In both personal and business applications, end-user devices hold a large amount of information. This information, if in the wrong hands, can often be used maliciously. We’ve reached a point where data is one of the most important assets we have. If your end-user devices lack a complex protection system, the data stored on them is vulnerable. Since end-user devices see the highest threats to cybersecurity attacks, it is vital to secure them with endpoint protection software.
In Business, Endpoints Grow as the Business Grows
Naturally, as a business grows, so does its amount of endpoints. The more you expand, the more devices you add. While antivirus software may be good for a single computer, it won’t be strong enough to handle several dozen to several hundred computers.
Another aspect of this growth that business has seen recently involves remote work. Remote workers using company devices or personal devices create vulnerability within the company. These end-user devices are not within the physical area for a company to protect. They may even be connected to open networks from time to time, and as such, they need more competent security options. The best security option for remote workers is endpoint security, that the company itself controls. It helps protect whatever device is storing and sending company information.
How Does Endpoint Security Work?
Endpoint security works by safeguarding the data and workflows of any end-user devices connected to your network. Endpoint protection platforms, also known as endpoint security programs, examine all files entering the network. Some of these platforms are on-site, contained in servers, while others are cloud-based.
The platforms contain a database of different known threats. As threats continue to update, so does the database. This is sometimes done via the cloud. Other times it is done by updating the on-site protection software. These updates help to prevent the end-user devices on the network from having to store this data individually. If each end-user device had to store threat information, they wouldn’t have room for much else. New threats are developed every day, making an updated form of security absolutely crucial to your data security.
Another benefit to cloud-based endpoint security is the scalability it provides. Because the data is free-flowing on the cloud, it doesn’t require manual updates to new end-user devices. All actions are available to administrators through a centralized console. This console is installed on a network gateway or a server that lets cybersecurity professionals control device securities remotely.
An endpoint that is set up on the endpoint platform allows administrators to do several things remotely. These things include:
- Pushing updates to devices (Learn more about the importance of software updates below)
- Authenticating log-in attempts on each device
- Administering corporate policies from a single location
- Blocking or removing applications known to be unsafe or unauthorized
- Encrypting information that is communicated through devices
Endpoint Protection is Fast
Endpoint protection allows companies to detect malware and threats on their devices quickly. It’s much faster than antivirus software, which is primarily passive. Endpoint security tends to be proactive, as it monitors all information sent to the network. In addition to endpoint platforms, there are also endpoint detection and response tools available. These components allow for the detection of more advanced threats. Some of those threats include file-less malware, polymorphic attacks, and zero-day attacks. Endpoint security systems employ continuous monitoring, which is the best way to achieve cybersecurity for your data.
Key Components of Endpoint Security Solutions
When choosing an endpoint security solution, most will come with the following key components:
- Machine-learning capabilities to identify zero-day threats in real time
- Antivirus and antimalware designed for protection of multiple devices
- Web browser security add-ons
- Data loss prevention
- Data classification
- An integrated firewall for blocking network attacks
- Phishing and social engineering protection with email gateways
- Centralized endpoint management for administrators and cybersecurity professionals
- Disk, email, and endpoint encryption
These are not the only components that a company may offer, but companies will often provide additional components at an added cost.
What is an Endpoint?
Generally speaking, endpoints are considered to be any connected device. Naturally, this includes desktop computers, laptop computers, tablets, and smartphones. However, it may also include a range of devices you wouldn’t consider: Smartwatches, printers, servers, ATMs, or connected medical devices can also be considered endpoints. While it may be hard to believe, all of these devices can store large amounts of sensitive information that can harm your business if used maliciously.
A considerable threat to companies right now is the bring-your-own-device (BYOD) mentality. With the majority of businesses operating remotely to an extent, BYOD has become far more popular. When a device is allowed to operate on a network, it has to be considered safe. If BYOD is an option for employees, then the devices they’re using will need to have protection software installed on them. Endpoint security makes this easy since it’s a connected form of security.
Mobile Devices Have Complicated Things
The flood of connected mobile devices over the last decade has complicated network security. Some individuals may have up to ten different end-user devices. It’s easier to reach than you may think, considering the options that people have. Smartphones, tablets, watches, e-readers, printers, and even medical devices may be able to connect to a network. If the network lacks endpoint security, it can transmit malicious software to other devices. Endpoint security helps to avoid that issue.
How is Endpoint Protection Different from Antivirus Software?
When reading through the information provided, you may think that both these options are pretty much the same. The thing that people recognize most often is that antivirus software came first. However, the two are very different from one another. Taking a look at them both in detail, side-by-side, is essential.
Antivirus Software: Out with the Old
Antivirus software is the oldest form of computer protection. It’s been on computers for decades at this point, and as such, has become somewhat antiquated. Antivirus is meant to prevent malware. Malware is a blanket term for anything that’s possibly harmful to your computer. It can refer to viruses, spyware, bots, worms, and keyloggers.
In most cases, antivirus software is installed directly on the end-user device. This allows it to run in the background and scan the device every so often for threats. However, it’s not as advanced as endpoint security. It relies on signature-based detection and prevention. As cybersecurity threats have evolved, they have become signature-less and file-less, specifically to bypass antivirus software.
Endpoint Security: In With the New
Endpoint security aims to fix the faults that antivirus software has, as discussed previously. Antivirus software cannot add the layers of protection that endpoint security can. It allows administrators to prevent the addition of another device to their networks. It also consistently updates to have the most protection at any given time. Most endpoint security options are antivirus software as well. As such, it’s the superior option.
Data Loss Prevention
Antivirus software doesn’t include any options for data loss prevention, while endpoint security does. By focusing on the data stored in endpoints, endpoint security can keep it safe. Data loss prevention protocols allow data to be monitored on your network. It can block any data from entering or exiting the network and can detect anomalies in data movement, which is ideal for keeping track of sensitive information that moves back and forth on your network. Data loss could be financially devastating and destructive for any business, so preventing this type of disaster is critical.
Sandboxing
Some threats are not easily identifiable by antivirus software or endpoint security platforms. They can be installed and begin wreaking havoc before any measures can be taken. Antivirus software has no protection against such threats. On the other hand, endpoint security has a method of handling any ambiguous data or programs being installed on end-user devices: sandboxing.
Before endpoint security allows the installation of a program on an end-user device, it will first isolate it. The endpoint platform will install the program onto a secure digital environment that mimics an end-user device in isolation. Here it will allow the program to run codes and execute files. This allows the platform to analyze the program and its intentions safely. Should the program clear the inspection and be deemed harmless, the endpoint security will allow installation on the end-user device. If anything suspicious occurs, the program is scrutinized, and remediation can occur.
Up-to-Date Firewalls
Like everything associated with endpoint security, the firewalls provided alongside it are updated and ready to stop any threats from entering your network. What’s more, is that these firewalls are connected to the platform and updated when need be. This keeps your network as safe as possible. It also allows for real-time analysis of any threats. Antivirus software cannot move as quickly as endpoint security, leaving your firewall exposed to threats.
Endpoint Detection and Response
Anomaly detection is the best feature of endpoint security platforms and a feature that no antivirus software can compete with. Endpoint detection and response is a protocol that continuously monitors the endpoints on your network. It can detect any strange happenings on your network. It has a significant advantage over antivirus software: detection.
Antivirus software can only block known threats. Endpoint protection can detect threats that already exist on any device connected to your network. Doing so allows it to seek threats out and stop them from functioning. Antivirus software cannot identify and block all threats, as it relies on signatures. If something were to make it past the antivirus software, it could not stop the malware from functioning. Endpoint security has a lower chance of letting a malicious program or file from entering a device to begin with. If something were to make it past the program, it could detect, isolate, and eliminate the threat in real-time.
Which is Better?
It comes down to your needs. If you have a single device that’s being used for sensitive information, you may be able to get away with antivirus software (Assuming it’s bolstered with other protection programs). However, it is unlikely that only one of your devices has sensitive information. Therefore, endpoint security should be heavily considered by most individuals or organizations. It provides the most safety and allows for continued protection. If you’re looking for the best security option for your data and devices, endpoint security is your best bet.
Want to learn more about your company’s security? To find out how your company is performing and isolate weaknesses in your cyber defenses, schedule a call with us or take our free, self-guided IT Security Risk Assessment .