Running a business is difficult work. There are so many factors you need to consider. One area of business that’s become increasingly more important is cybersecurity. Cyber-attacks are on the rise, so you’ll need to do everything you can to protect your company.
Cybercriminals are always looking for ways they can exploit organizations. One of the main ways they like to manipulate people is by taking advantage of human error. So, what exactly is human error in cybersecurity, and how can you protect your company?
This article explains some of the different kinds of human error that affect cybersecurity and offers security tips to help keep your company safe.
Physical Security Errors
Many people don’t consider physical security a part of cybersecurity. However, cybercriminals often resort to “real-world tactics” as companies are increasingly paying attention to things like firewalls, antivirus software, and data backups. If a criminal can physically get into your company property, they can damage your digital infrastructure. For example, they could install new keyboards that log keystrokes, insert malicious USB sticks into workstations, or simply walk out with sensitive hardware.
Letting unauthorized people into your company offices is a significant human error that can compromise your organization’s security. Given that this type of error could lead to a significant security breach, you’ll need to take measures to minimize this threat. For example, you might require employee swipe cards or use specific keys or access codes to enter the premises. You also need to ensure your employees know that letting unauthorized people into the offices poses a risk to the organization.
Another physical security error is when employees don’t properly secure the site. For example, they might go home without locking doors properly. This could allow unauthorized people to get in and access the computer systems. You can mitigate these kinds of problems by having clear expectations and responsibilities laid out. Everyone should know basic security rules and know who is responsible for locking up the property at the end of the workday.
Skill-Based Errors
In small-to-medium-sized businesses, people often make skill-based errors. This is when someone performs a task incorrectly, potentially causing a security risk. For example, a worker might fail to correctly set up antivirus software on their workstation. Or they might turn off the antivirus protection entirely. You can minimize these skill-based errors by reducing the control workers have over their workstations. You should have clear administrator privileges set up. This means people won’t be able to tamper with the antivirus software unless they work for the IT department.
Skill-based errors don’t necessarily happen because an employee is incompetent. These errors often occur because an employee is tired or distracted. This means you can reduce skill-based mistakes by making sure your workers are not fatigued or overworked.
This type of error can also occur when employees don’t have the correct training or if they’ve been dishonest about their level of experience. As an employer, you must always ensure your workers have the skills they need to do the job. If your employees’ IT skills are lacking, you should consider training seminars or training courses. Not only will this help protect your company against cyber-attacks, but it will also help your workers develop their skills and become better professionals.

Decision-Based Errors
Decision-based errors are another kind of error that could impact business protection. This is when an employee makes a decision that leads to a security issue. For example, someone might open a file that installs ransomware on the company network. Someone could also plug in a USB stick that was infected with a virus.
If you want to reduce decision-based errors in your workplace, you need to prevent people from making poor security decisions. This means your staff will need to understand security risks well. You can do this by having security seminars and a clear security policy in your employee handbook.
Another solution is to have systems in place that prevent risky behavior. For example, you might prevent people from being able to plug in USB sticks or open EXE files.
Misdelivery
Misdelivery is a form of human error where someone sends files, documents, or information to the wrong person. This can be a significant problem if your company deals with confidential data. If misdelivery occurs, you’ll need to disclose the data breach to your customers, which could impact your company’s reputation and lead to less business in the future.
You can combat this by ensuring there are clear procedures for working with confidential information and ensuring you are compliant with security standards.
Password Problems
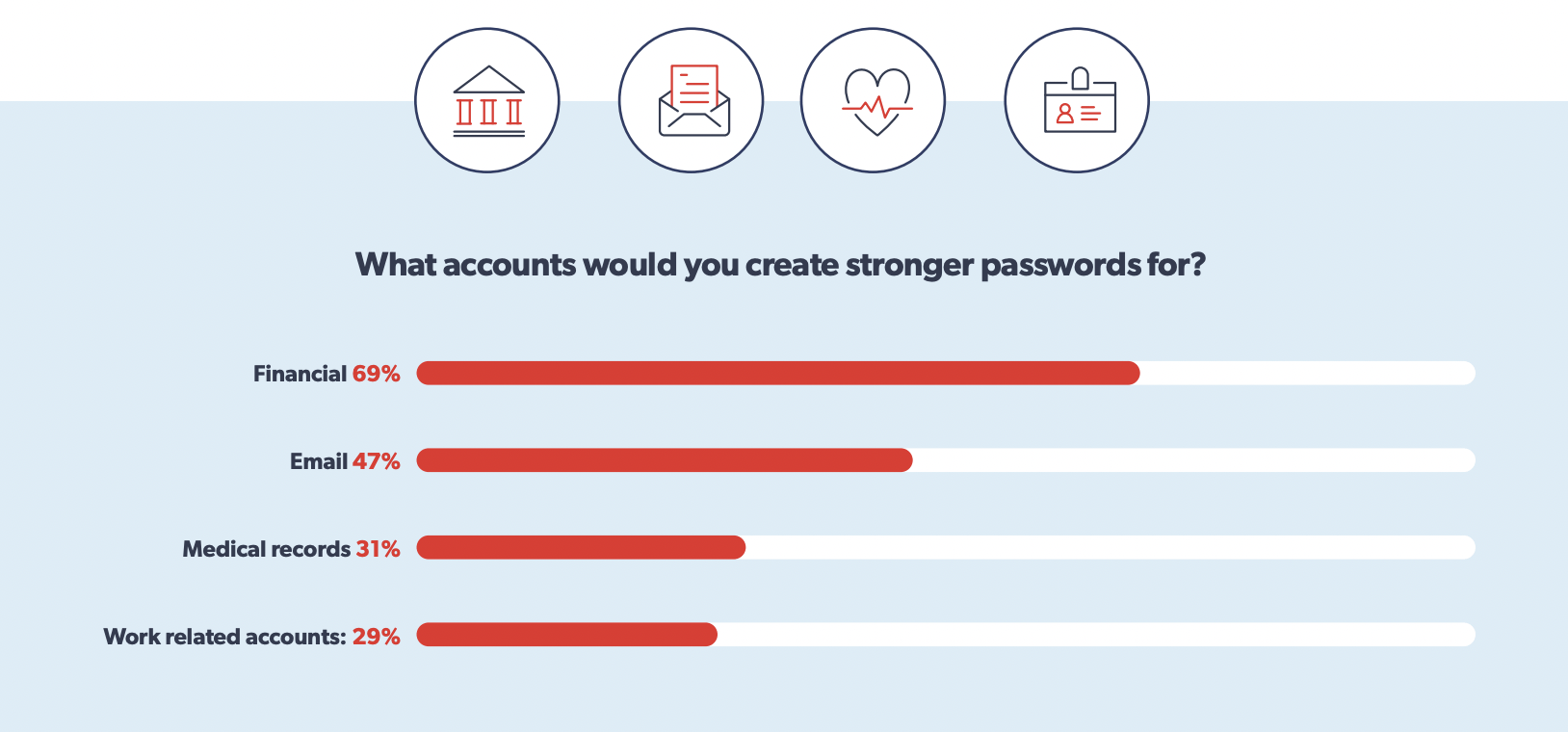
Another form of human error relates to passwords. Everyone knows that you need to have unique, strong passwords, but few people put this into practice. In fact, around 56% of people reuse the same password across multiple services.
When people do this with their work account, it introduces a problem. You can’t control what your workers do in their personal lives. If someone is using the same password at home and on their personal accounts, it’s a significant risk. If hackers get into their personal account using their password, it’s possible they will try the password across other services. This will enable hackers to breach your systems.
One of the best ways to deal with this is by having a good password policy. Having mandatory password changes every few months makes it much less likely that people will use the same passwords they use in their personal life.
Another potential solution is using multi-factor authentication. This is when you need both your password and a verification code to log on. When you input your password, a verification code is sent to a second device or service. For example, you might receive the code as a cell phone text message.
This is a great policy as it eliminates a lot of the risk of human error. Even if hackers have an employee’s password, they still can’t break in without the code.
Social Engineering
Another way hackers use human error to their advantage is through social engineering. Social engineering is when hackers use clever psychological tricks to manipulate people into compromising their security.
For example, someone might call an employee pretending to be the CEO. If the employee falls for this technique, it’s a serious human error. Social engineering is very prevalent because it exploits well-known weaknesses in human psychology. These attacks often convey a sense of critical urgency. If a situation feels urgent, people are much more likely to make a mistake and compromise on security.
In the last decade, most companies have stepped up their game in terms of cybersecurity. Most companies run robust firewalls and antivirus software, but none of this matters if a hacker uses social engineering techniques. Social engineering techniques are so prevalent in cybercrime that some statistics suggest hackers use social engineering in around 98% of attacks. The only way to protect your company is to make sure your employees understand how these attacks work.
The only real solution here is to have frequent security training. Your employees need to recognize social engineering and have someone they can report suspicious behavior to.
Human error is much more likely if people feel their reports won’t be taken seriously or if they’ll get in trouble for reporting a false positive. Creating a strong security culture in your organization is the best way to reduce human errors.
Take the Necessary Steps to Reduce Human Error
To conclude, you need to understand that some level of human error is inevitable. With that said, this article has shown there are many measures you can take to reduce the risk. You can have strong security policies, set up permissions systems, and create a strong security culture.
Of course, setting up strong cyber defenses is a very complex task. The world of cybersecurity is constantly changing, and it’s a full-time job in itself to monitor emerging threats.
With this in mind, working with a managed IT services company makes a lot of sense to help safeguard your company. If you want to work with such a company, contact us today and take the first steps in protecting against human error and securing your business.